Cryptography
This example shows how to encrypt/decrypt a text.
Hardware
No hardware is needed for this example. You can run it without being logged in.
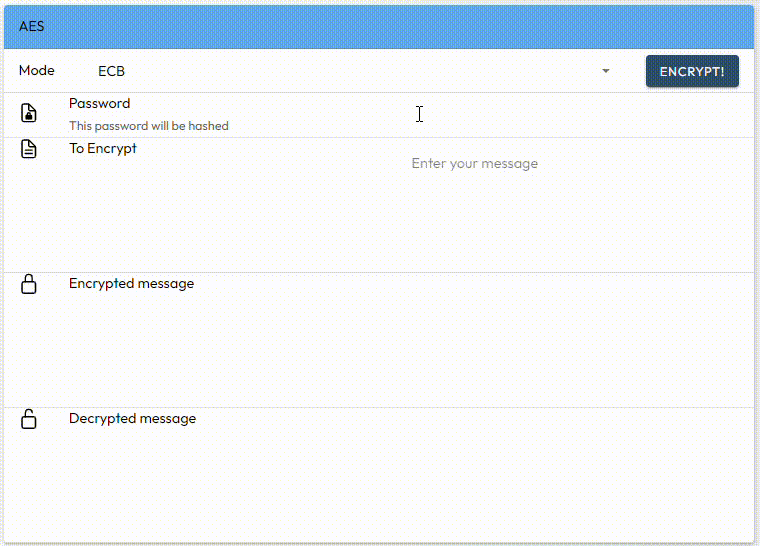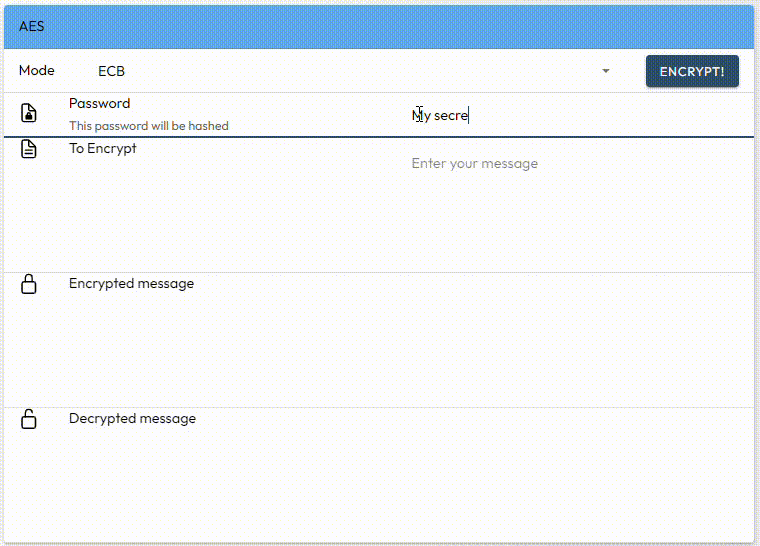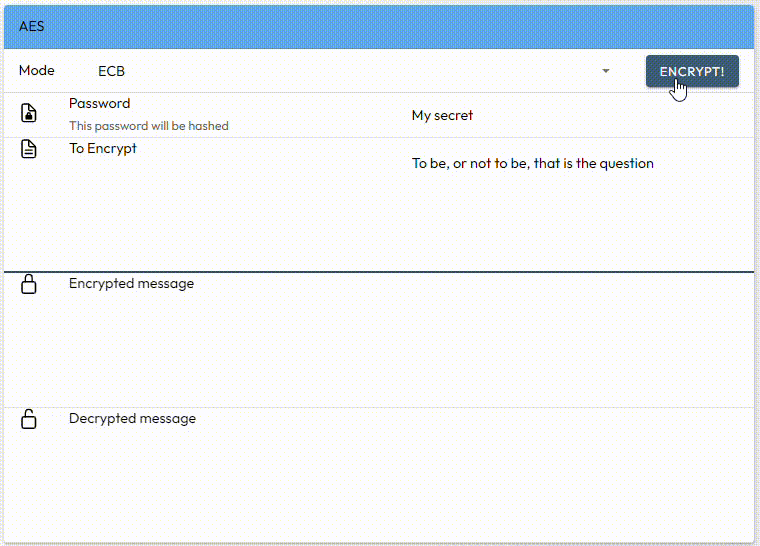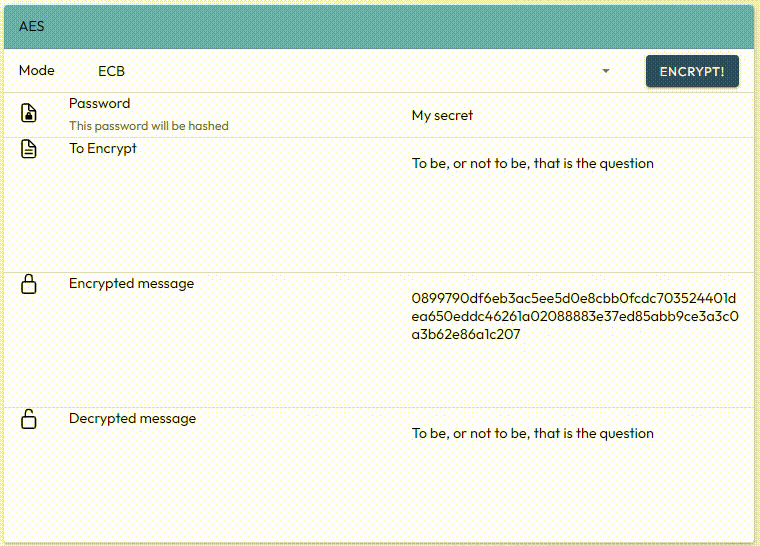
UI components
The UI allows you to enter the key (password) and the text to be encrypted. The entered password is optionally hashed to generate the key that will be used for encryption. The algorithm is selectable from ECB, CTR, CBC, GCM and CFB.
💡 Note:
-
When no hash requested, the key must be 16 bytes long
-
Depending on the algorithm, options (IV, ...) must be set.
Dataflow graph
The dataflow shows how to use the cryptographic nodes (SHA, Encrypt and Decrypt). CRC16-CCITT calculation is also performed (into an inline node) and displayed. However, this value is not inserted into the data to be encrypted.